Testing.
Sunday, November 15, 2009
Sunday, April 26, 2009
Data Comm.
Layers of TCP/IP
- Application
- Transport
- Network
- Data link
- Physical
Layer 7: The application layer - The application layer is responsible for providing services to the user.
This is the layer at which communication partners are identified, quality of service is identified, user authentication and privacy are considered, and any constraints on data syntax are identified. (This layer is not the application itself, although some applications may perform application layer functions.)
Layer 6: The presentation layer-This is a layer, usually part of an operating system, that converts incoming and outgoing data from one presentation format to another (for example, from a text stream into a popup window with the newly arrived text). Sometimes called the syntax layer.
Layer 5: The session layer-This layer sets up, coordinates, and terminates conversations, exchanges, and dialogs between the applications at each end. It deals with session and connection coordination.
Layer 4: The transport layer-
The transport layer is responsible for delivery of a message from one process to another.
This layer manages the end-to-end control (for example, determining whether all packets have arrived) and error-checking. It ensures complete data transfer.
Layer 3: The network layer-
The network layer is responsible for the delivery of packets from the original source to the
final destination. This layer handles the routing of the data (sending it in the right direction to the right destination on outgoing transmissions and receiving incoming transmissions at the packet level). The network layer does routing and forwarding.
Layer 2: The data-link layer-
The data link layer is responsible for transmitting frames from
one node to the next. This layer provides synchronization for the physical level and does bit-stuffing for strings of 1's in excess of 5. It furnishes transmission protocol knowledge and management.
Layer 1: The physical layer- The physical layer is responsible for transmitting individual bits from one node to the next. This layer conveys the bit stream through the network at the electrical and mechanical level. It provides the hardware means of sending and receiving data on a carrier.
Signals can be analog or digital. Analog signals can have an infinite number of values in a range; digital signals can have only a limited number of values.
Time and frequency domains
The bandwidth is a property of a medium: It is the difference between the highest and the lowest frequencies that the medium can satisfactorily pass.
Bit rate and bit interval
Error Detection and Correction
Detection
- A simple method of error detection is required to maintain data integrity
- The challenge in error detection is recognizing the different types of errors that occur in a simple and objective manner
Redundancy
Redundancy means adding extra bits for detecting errors at the destination.
There are 4 types of redundancy checks:
- vertical redundancy check (VRC)
- VRC can detect all single-bit errors.
- VRC can detect multiple-bit and burst errors only if the total number of errors is odd.
- Longitudinal redundancy check (LRC).
- Can detect multiple-bit and burst-errors.
- Cannot detect errors where an even number of bits are inverted.
- Cyclic redundancy check (CRC).
- Requires the addition of a frame check sequence (FCS) or error-detecting code to each synchronous frame.
- Performs a complex mathematical operation on the data (based on binary division).
- Message is treated as one long binary number.
- Divides entire numeric binary value of the block of data by a constant called a generator polynomial(n+1 bits).
- Quotient is discarded, and the remainder (the CRC) is appended to the block and transmitted along with the data.
- The receiver divides the data unit by the same number. If there is no remainder, message is intact.
- checksum
- The error detection method used by the higher layer protocols of the OSI model is called checksum .
- Computing a sum based upon the ASCII character
Error Correction
VRC, LRC, checksum, and CRC are effective in detecting errors, but cannot automatically correct the data.
- Error correcting codes are more sophisticated than error-detection codes and require more redundancy bits.
- The number of bits required correcting a multiple-bit or burst error is so high that it becomes too inefficient to correct.
Single-Bit Error Correction
- The object of error correction is to locate the invalid bit or bits.
- A redundancy code should adequately reflect all possible error locations.
Hamming Code
- The Hamming code is a method of error detection and error correction.
- These redundancy bits are a function of the length of the data bits.
- For a data unit of m bits, the formula 2 r > m + r + 1 to determine r , the number of redundant bits needed.
- Each r bit is the VRC bit for one combination of data bits; r 2 is the VRC bit for another combination of data bits, etc. (e.g. a 7-bit ASCII string would require 4 redundancy bits)
- The receiver recalculates the VRC using the same sets of bits used by the sender plus the relevant parity ( r ) bit for each set.
- It then assembles the new parity values into a binary number in order of r position.
- Once a bit error is detected, the receiver can reverse its value and correct the error.
Single-bit error
Error
Detection
Multiple-Bit Error Correction
- Redundancy bits calculated on overlapping sets of data bits can also be used to correct multiple-bit errors.
- Requires more sophisticated schemes.
5 component of data communication:
- Sender
- Receiver
- Medium
- Massage
- Protocol
Type of Data Flow:
- Simplex : mainframe to monitor only
- Half duplex: between 2 workstation one direction way at one time.
- Full duplex: both directions at one time.
2 type of connection:
- Point to point
- Multipoint
4 type of topology:
- Mesh
- Star
- Bus
- Ring
______________________________________________________
Chaper 2
Sunday, February 15, 2009
The Differences Between Hubs, Switches and Routers
Some technicians have a tendency to use the terms routers, hubs and switches interchangeably. One minute they're talking about a switch. Two minutes later they're discussing router settings. Throughout all of this, though, they're still looking at only the one box. Ever wonder what the difference is among these boxes? The functions of the three devices are all quite different from one another, even if at times they are all integrated into a single device. Which one do you use when? Let's take a look...
Hub, Switches, and Routers: Getting Started with Definitions
Hub
A common connection point for devices in a network. Hubs are commonly used to connect segments of a LAN. A hub contains multiple ports. When a packet arrives at one port, it is copied to the other ports so that all segments of the LAN can see all packets.
Switch
In networks, a device that filters and forwards packets between LAN segments. Switches operate at the data link layer (layer 2) and sometimes the network layer (layer 3) of the OSI Reference Model and therefore support any packet protocol. LANs that use switches to join segments are called switched LANs or, in the case of Ethernet networks, switched Ethernet LANs.
Router
A device that forwards data
packets along networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP.s network. Routers are located at gateways, the places where two or more networks connect. Routers use headers and forwarding tables to determine the best path for forwarding the packets, and they use protocols such as ICMP to communicate with each other and configure the best route between any two hosts.
The Differences Between These Devices on the Network
Today most routers have become something of a Swiss Army knife, combining the features and functionality of a router and switch/hub into a single unit. So conversations regarding these devices can be a bit misleading — especially to someone new to computer networking.
The functions of a router, hub and a switch are all quite different from one another, even if at times they are all integrated into a single device. Let's start with the hub and the switch since these two devices have similar roles on the network. Each serves as a central connection for all of your network equipment and handles a data type known as frames. Frames carry your data. When a frame is received, it is amplified and then transmitted on to the port of the destination PC. The big difference between these two devices is in the method in which frames are being delivered.
In a hub, a frame is passed along or "broadcast" to every one of its ports. It doesn't matter that the frame is only destined for one port. The hub has no way of distinguishing which port a frame should be sent to. Passing it along to every port ensures that it will reach its intended destination. This places a lot of traffic on the network and can lead to poor network response times.
Additionally, a 10/100Mbps hub must share its bandwidth with each and every one of its ports. So when only one PC is broadcasting, it will have access to the maximum available bandwidth. If, however, multiple PCs are broadcasting, then that bandwidth will need to be divided among all of those systems, which will degrade performance.
A switch, however, keeps a record of the MAC addresses of all the devices connected to it. With this information, a switch can identify which system is sitting on which port. So when a frame is received, it knows exactly which port to send it to, without significantly increasing network response times. And, unlike a hub, a 10/100Mbps switch will allocate a full 10/100Mbps to each of its ports. So regardless of the number of PCs transmitting, users will always have access to the maximum amount of bandwidth. It's for these reasons why a switch is considered to be a much better choice then a hub.
Routers are completely different devices. Where a hub or switch is concerned with transmitting frames, a router's job, as its name implies, is to route packets to other networks until that packet ultimately reaches its destination. One of the key features of a packet is that it not only contains data, but the destination address of where it's going.
A router is typically connected to at least two networks, commonly two Local Area Networks (LANs) or Wide Area Networks (WAN) or a LAN and its ISP's network . for example, your PC or workgroup and EarthLink. Routers are located at gateways, the places where two or more networks connect. Using headers and forwarding tables, routers determine the best path for forwarding the packets. Router use protocols such as ICMP to communicate with each other and configure the best route between any two hosts.
Today, a wide variety of services are integrated into most broadband routers. A router will typically include a 4 - 8 port Ethernet switch (or hub) and a Network Address Translator (NAT). In addition, they usually include a Dynamic Host Configuration Protocol (DHCP) server, Domain Name Service (DNS) proxy server and a hardware firewall to protect the LAN from malicious intrusion from the Internet.
All routers have a WAN Port that connects to a DSL or cable modem for broadband Internet service and the integrated switch allows users to easily create a LAN. This allows all the PCs on the LAN to have access to the Internet and Windows file and printer sharing services.
Some routers have a single WAN port and a single LAN port and are designed to connect an existing LAN hub or switch to a WAN. Ethernet switches and hubs can be connected to a router with multiple PC ports to expand a LAN. Depending on the capabilities (kinds of available ports) of the router and the switches or hubs, the connection between the router and switches/hubs may require either straight-thru or crossover (null-modem) cables. Some routers even have USB ports, and more commonly, wireless access points built into them.
Some of the more high-end or business class routers will also incorporate a serial port that can be connected to an external dial-up modem, which is useful as a backup in the event that the primary broadband connection goes down, as well as a built in LAN printer server and printer port.
Besides the inherent protection features provided by the NAT, many routers will also have a built-in, configurable, hardware-based firewall. Firewall capabilities can range from the very basic to quite sophisticated devices. Among the capabilities found on leading routers are those that permit configuring TCP/UDP ports for games, chat services, and the like, on the LAN behind the firewall.
So, in short, a hub glues together an Ethernet network segment, a switch can connect multiple Ethernet segments more efficiently and a router can do those functions plus route TCP/IP packets between multiple LANs and/or WANs; and much more of course.
Saturday, January 24, 2009
(Networking Basics): TCP, UDP, TCP/IP & OSI models
The Transmission Control Protocol/Internet Protocol (TCP/IP) suite was created by the U.S. Department of Defense (DoD) to ensure that communications could survive any conditions and that data integrity wouldn't be compromised under malicious attacks.
The Open Systems Interconnection Basic Reference Model (OSI Model) is an abstract description for network protocol design, developed as an effort to standardize networking.
Comparing TCP/IP and the OSI Models
The TCP/IP model is basically a shorter version of the OSI model. It consists of four instead of seven layers. Despite their architectural differences, both models have interchangeable transport and network layers and their operation is based upon packet-switched technology. The diagram below indicates the differences between the two models:
Application Layer: The Application layer deals with representation, encoding and dialog control issues. All these issues are combined together and form a single layer in the TCP/IP model whereas three distinctive layers are defined in the OSI model.
Host-to-Host: Host-to-Host protocol in the TCP/IP model provides more or less the same services with its equivalent Transport protocol in the OSI model. Its responsibilities include application data segmentation, transmission reliability, flow and error control.
Internet: Again Internet layer in TCP/IP model provides the same services as the OSIs Network layer. Their purpose is to route packets to their destination independent of the path taken.
Monday, January 19, 2009
ASCII Character Code List
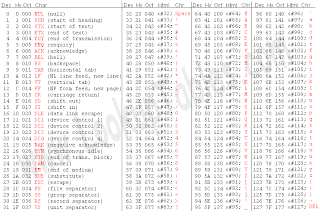
ASCII stands for American Standard Code for Information Interchange. Computers can only understand numbers, so an ASCII code is the numerical representation of a character like 'c' or '#' or an action of some sort. Here are some sample ASCII codes and the characters they represent:
033 -- !
So for example the code '035' will give you the character: #
Examples would include: ™ ¾ ®
2. Type the ASCII number code.
3. Let go of the"ALT" key.
Dreamweaver MX also has a 'Character' tab at the top of the window with many of these codes for you you to use.
The HTML equivalent to the ASCII code is simply: An ampersand and hash before the ASCII number and semicolon following the ASCII number. So for example the ASCII code for $ (dollar sign) is the number 36, so the the HTML code for this is:
$
Please note than when using the ASCII codes you need to always start with the number 0 (zero) then the code. So to get $ you need to type in 036 and not just 36.
UNICODE
These encoding systems also conflict with one another. That is, two encodings can use the same number for two different characters, or use different numbers for the same character. Any given computer (especially servers) needs to support many different encodings; yet whenever data is passed between different encodings or platforms, that data always runs the risk of corruption.
Unicode provides a unique number for every character, no matter what the platform, no matter what the program, no matter what the language. The Unicode Standard has been adopted by such industry leaders as Apple, HP, IBM, JustSystems, Microsoft, Oracle, SAP, Sun, Sybase, Unisys and many others. Unicode is required by modern standards such as XML, Java, ECMAScript (JavaScript), LDAP, CORBA 3.0, WML, etc., and is the official way to implement ISO/IEC 10646. It is supported in many operating systems, all modern browsers, and many other products. The emergence of the Unicode Standard, and the availability of tools supporting it, are among the most significant recent global software technology trends.
Incorporating Unicode into client-server or multi-tiered applications and websites offers significant cost savings over the use of legacy character sets. Unicode enables a single software product or a single website to be targeted across multiple platforms, languages and countries without re-engineering. It allows data to be transported through many different systems without corruption.
3. E-mail
4. Web
5. Fonts
6. New lines





